[ad_1] He also writes on Blue, select a security vulnerability in VerizonIPHONE and iOS calls application, which allows a bad representative to reach the call record records for Verizon Users. At the heart of the problem, there was a weakness in how to request the application and receive call record data. When users open the application to view modern calls, it will send a request to a distant server, select the user's phone number and request the records match. This should have been tightly restricted, so the person who logged into the app can only see his own data. An example of a weak request. | Credit image - Ivan Connect It turns out that the back interface of the application failed to properly verify that the request is coming from the actual account holder. This means that the curious actor - or the malicious - can change the request for another person's number and receive his call record. There are no passwords, no, then, just a number and a few knowledge. What's more, it seems that the system behind this defect has been managed directly VerizonBut through a less well -known company called CEQUINT, which specializes in the calling ID technology. This raises additional questions about the amount of user data that is dealt with by third parties - and the extent of this data is already securing. Ivan was found and reported in February 2025. Verizon Since the problem has been repaired since then, but exposure could have affected many users, especially since the call candidate is likely to be active by default for most Verizon Customers. It is a blatant reminder that even the simple verb to verify what he called you should not come at the expense of your privacy.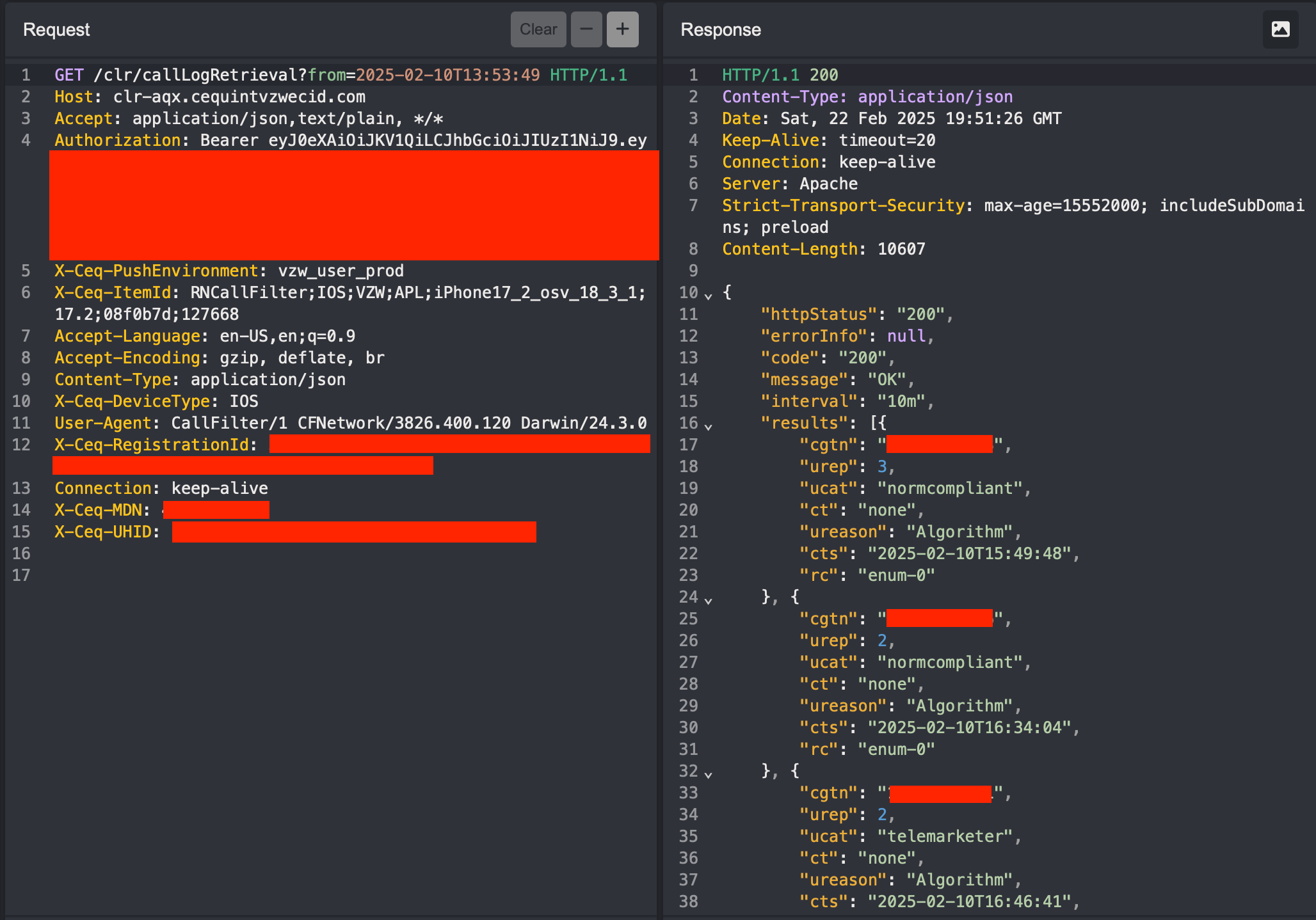

[ad_2]
Download
Verizon glitch put users’ call logs in the wrong hands, sparks real-time surveillance worries
| Name | |
|---|---|
| Publisher | |
| Genre | News & Magazines |
| Version | |
| Update | April 5, 2025 |
| Get it On |  |